Service hotline
+86 0755-83044319
release time:2022-03-17Author source:SlkorBrowse:11096
With the appearance and development of LSI, MCU integrates the CPU, RAM, ROM, timer counter and various I/O interfaces of the original computer into one chip, thus forming a chip-level computer. This is also the prototype of TMS 1000 series (below), the world's first microcontroller (MCU) invented by Gary Boone and Michael Cochran of TI engineers. After that, Japanese electronics manufacturers began to produce automotive microcontrollers, including 4-bit MCU for in-car entertainment, automatic wipers, electronic locks and instrument panels, and 8-bit MCU for engine control.

* TMS 1000 series MCU of TI *
Today, apart from the traditional toy market, industrial control, automotive electronics, white goods, etc., with the advent of the Internet of Things and the wave of intelligence, MCU has become the core component of product equipment. On the one hand, the equipment needs real-time efficient and intelligent information, and on the other hand, it can exchange information with other equipment. All these requirements need to be completed by MCU. It can be said that MCU is born of application. Besides the hardware performance of the chip itself, the application-related program firmware becomes more and more important, and the demand for firmware security is getting more and more attention!
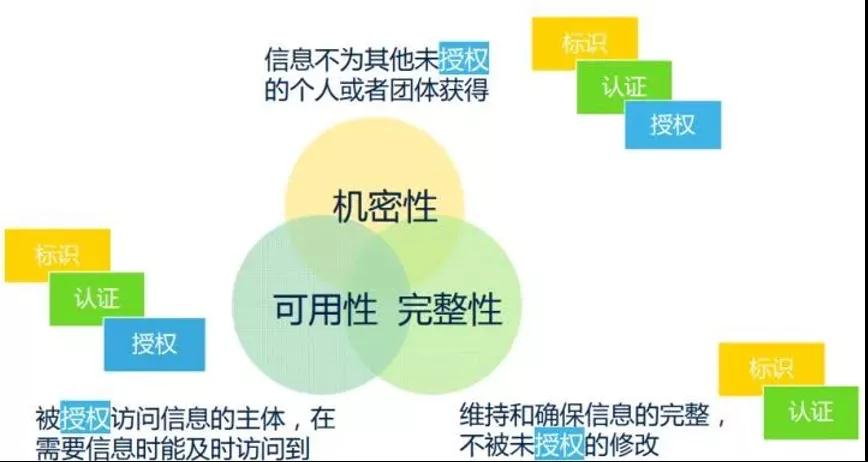
First of all, "security" in a broad sense can also be regarded as "information security", which has three important characteristics:
1. confidentiality: it is necessary to ensure that the information is not obtained by other unauthorized individuals or groups.
2. Integrity: Maintain and ensure the integrity of information and prevent unauthorized tampering.
3. Feasibility: the subject authorized to access information can access and obtain information in time when it is needed.
Confidentiality, Integrity, integrity and feasibilityAvailability, referred to as CIA
From the above description, three common tools for dealing with information security are derived: identification, authentication and authorization, also referred to as IAA for short.
1) Identity: identityFirst, the information visitor indicates the identity of the subject, but is not sure that the subject can actually access the information? Therefore, it is necessary to verify its authenticity;
2) Authentication: AuthenticationAuthentication is to verify whether the content claimed by the subject is true. So as to make more detailed actions after the identity of the subject is verified.
3) Authorization: authorization
As a more detailed information processing, the problems to be solved include: What information can be viewed by the authorized person? Is the viewed information intact and not modified without authorization? And the authorized person can conveniently access the viewable information at any time.
For the three elements of information security and the relationship among the three tools, please refer to the following figure:
Generally, MCU has internal program area and data area for users to store programs and working data. In order to prevent unauthorized access to or copying of the programs in the MCU, most microcontrollers have encryption locks or encrypted bytes to protect the programs on the chip. If the positioning of the encryption lock is enabled (locked) during programming, it is impossible to directly read the program in the single-chip microcomputer with ordinary programmer, which is called single-chip microcomputer encryption.
With the help of special equipment or self-made equipment, the attacker can extract the key information from the chip and obtain the program in the chip through various technical means, which is called decryption of the chip. At present, common decryption methods of single chip microcomputer mainly include:
(1) Software attack: This technology usually uses processor communication interface and makes use of protocols, encryption algorithms or security vulnerabilities in these algorithms to attack. A typical example of successful software attack is the attack on the early ATMEL AT89C51 single-chip microcomputer. The attacker took advantage of the loopholes in the sequence design of erasing operation of this series of single-chip microcomputers, and stopped the next step of erasing the data in the on-chip program memory by using the self-compiled program after the encryption lock was located, so that the encrypted single-chip microcomputer became an unencrypted single-chip microcomputer, and then read out the on-chip program by using the programmer.
(2) Electronic detection attackThis technology usually monitors the analog characteristics of all power supplies and interface connections of the processor in normal operation with high time resolution, and carries out attacks by monitoring its electromagnetic radiation characteristics. Because the single chip microcomputer is an active electronic device, when it executes different instructions, the corresponding power consumption of the power supply changes accordingly. In this way, by using special electronic measuring instruments and mathematical statistical methods to analyze and detect these changes, the specific key information in the single chip microcomputer can be obtained.
(3) Fault generation technologyThis technology uses abnormal working conditions to make the processor error, and then provides additional access to attack. The most widely used fault occurs, and the attack means include voltage shock and clock shock. Low-voltage and high-voltage attacks can be used to disable the protection circuit or force the processor to perform wrong operations. Transient clock jump may reset the protection circuit without damaging the protected information. And power supply transient jump can affect the decoding and execution of a single instruction in some processors.
(4) Probe technology
This technology is to directly expose the internal connection of the chip, and then observe, manipulate and interfere with the single chip microcomputer to achieve the purpose of attack.
For convenience, people divide the above four attack technologies into two categories, one is intrusive attack (physical attack), which needs to destroy the package, and then it takes hours or even weeks to complete in a special laboratory with the help of semiconductor test equipment, microscope and micro-positioner. All microprobe technologies are intrusive attacks. The other three methods are non-invasive attacks, and the attacked MCU will not be physically damaged.

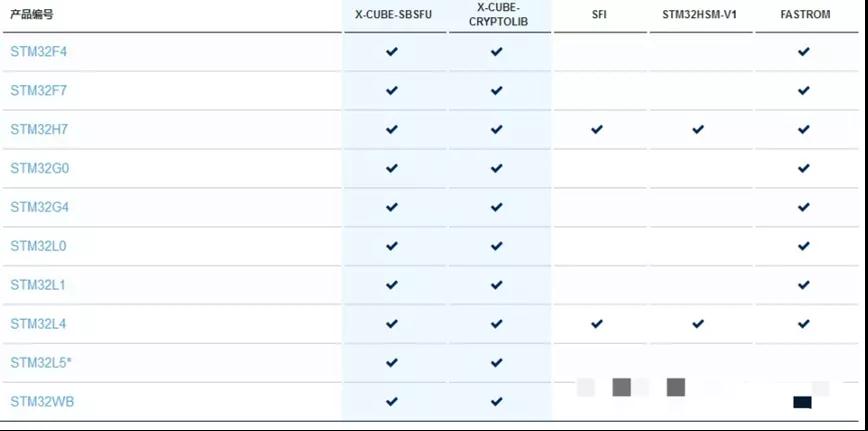
In view of the above decryption methods, in order to avoid the loss of users, all the original manufacturers have started from their own chips and strengthened the security level of the chips. For example, the STM32 Trust solution first proposed by STM 32 provides a complete suite of code protection and execution protection tools, but the types of covered chips are limited and the prices of corresponding chips are different.
At the same time, the solution delivery will involve many links, including agents, solution companies, burning factories and processing factories, etc. The existing single debugging or burning tools can't meet the safety control of the whole delivery chain.
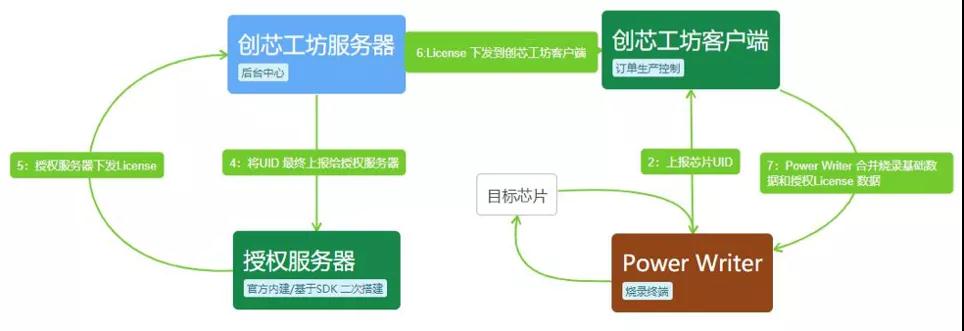
Aiming at this pain point, Chuangxin Workshop (ICWORKSHOP.com) put forward the concept of cloud delivery of program firmware for the first time in 2017, and implemented it online. Build a reliable and safe delivery platform between the program developer/solution company and the end user, and bind the firmware with the number of burning times, so as to protect the intellectual property rights of developers and benefit both parties.
Introduction of GD-Link Cloud Delivery: http://www.gd32mcu.com/cn/detail/289
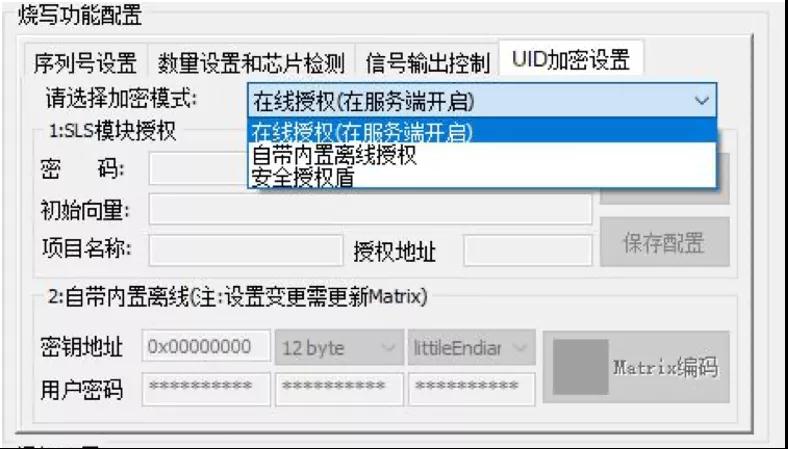
At the same time, with various encryption mechanisms provided by PowerWriter programming device, the function of "one core and one secret" is also realized without upgrading the chip level! At the same time, with the offline (UID binding) and online authorization and other encryption methods provided by PowerWriter programming device, the difficulty of chip cracking is greatly improved.
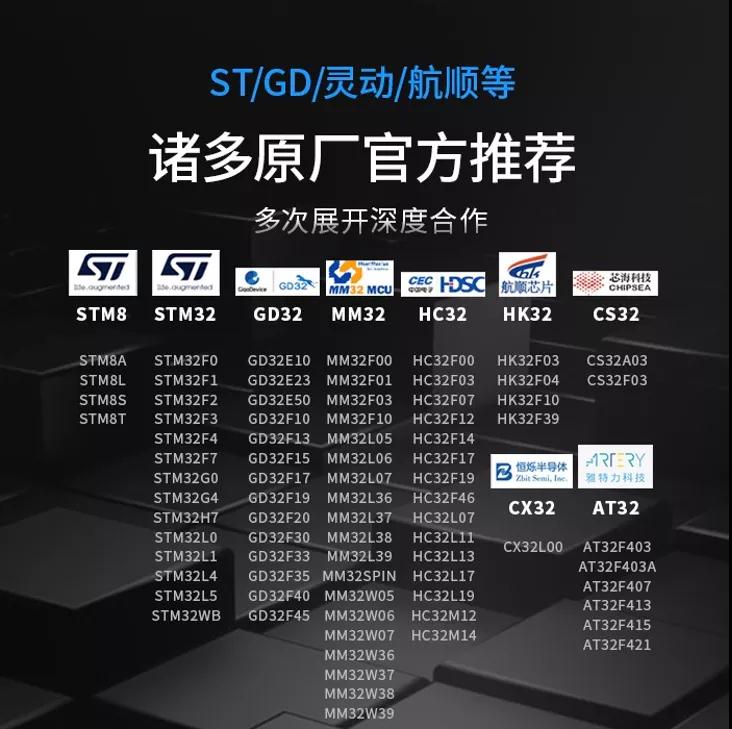
At the beginning of the year 2021, PowerWriter passed on good news in programming device. At present, it has completed eight single-chip brands, including STM8, STM32, GD32, MM32, HC32, HK32, CX32, CS32 and AT32, with more than 600 series and tens of millions of chip models. Welcome to visit www.powerwriter.cn for more information!
"ICWORKSHOP Chuangxin Workshop" is referred to as ICW for short, which stands for Innovation+Creativity+Wealth, respectively. It helps MCU developers, stimulates their creative spirit, and escorts their creativity, thus embodying the value of intellectual property rights!
Note: This article is reproduced from the Internet to support the protection of intellectual property rights. Please indicate the original source and author when reprinting. If there is any infringement, please contact us to delete it.
Company Tel: +86-0755-83044319
Fax/fax:+86-0755-83975897
Email: 1615456225@qq.com
QQ: 3518641314 Manager Li
QQ: 332496225 Manager Qiu
Address: Room 809, Block C, Zhantao Technology Building, No.1079 Minzhi Avenue, Longhua New District, Shenzhen



Site Map | 萨科微 | 金航标 | Slkor | Kinghelm
RU | FR | DE | IT | ES | PT | JA | KO | AR | TR | TH | MS | VI | MG | FA | ZH-TW | HR | BG | SD| GD | SN | SM | PS | LB | KY | KU | HAW | CO | AM | UZ | TG | SU | ST | ML | KK | NY | ZU | YO | TE | TA | SO| PA| NE | MN | MI | LA | LO | KM | KN
| JW | IG | HMN | HA | EO | CEB | BS | BN | UR | HT | KA | EU | AZ | HY | YI |MK | IS | BE | CY | GA | SW | SV | AF | FA | TR | TH | MT | HU | GL | ET | NL | DA | CS | FI | EL | HI | NO | PL | RO | CA | TL | IW | LV | ID | LT | SR | SQ | SL | UK
Copyright ©2015-2025 Shenzhen Slkor Micro Semicon Co., Ltd